Harnessing Webhooks in Kubernetes: A Comprehensive Guide
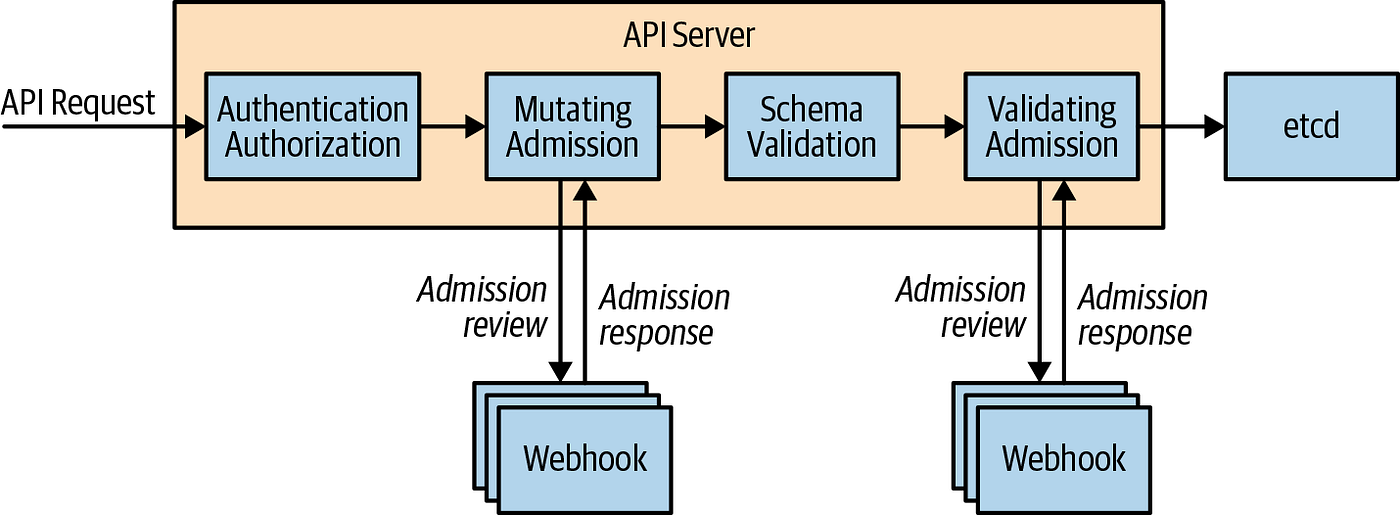
Kubernetes, the cornerstone of modern container orchestration, offers a plethora of features aimed at simplifying deployment, scaling, and operations of application containers. Among its numerous features, webhooks stand out as a powerful tool for extending Kubernetes functionality in a dynamic and automated fashion. This guide delves into the world of webhooks within Kubernetes, highlighting their significance, types, and practical applications to enhance your cluster’s operations.
Understanding Webhooks in Kubernetes
Webhooks in Kubernetes are HTTP callbacks that occur when a specific event happens. They are a critical component for extending Kubernetes’ capabilities, allowing external services to be notified about cluster events in real time. Webhooks come in two primary forms: Admission Webhooks and Mutating Webhooks.
Admission Webhooks
Admission webhooks are invoked before an object is persisted in the Kubernetes cluster. They serve as a powerful mechanism to enforce policies and ensure that the cluster state complies with the organization’s standards. Admission webhooks can be of two types: Validating Admission Webhooks and Mutating Admission Webhooks.
-
Validating Admission Webhooks: They inspect the requests to the Kubernetes API server and determine if the request should be allowed based on specific criteria. If the request violates any policy, it is rejected, and the user is notified.
-
Mutating Admission Webhooks: They not only inspect the requests but can also modify the objects sent to the API server. This is useful for enforcing default values, correcting minor errors in requests, or adding annotations automatically.
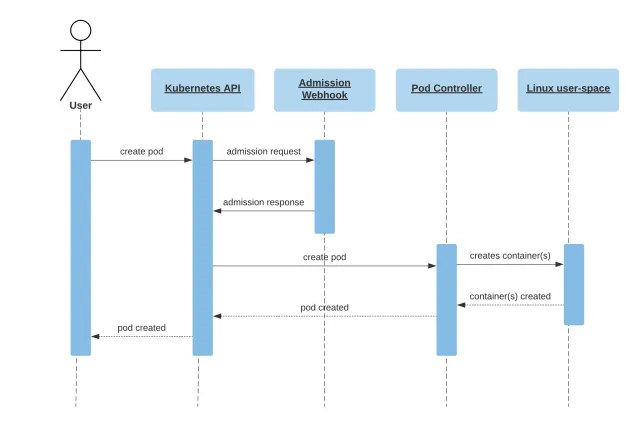
Implementing Webhooks in Your Cluster
To implement webhooks in your Kubernetes cluster, you need to:
-
Develop Your Webhook Server: This server listens for webhook calls from the Kubernetes API server. It can be written in any programming language as long as it can process HTTP requests.
-
Configure the Webhook in Kubernetes: This involves creating a
MutatingWebhookConfigurationorValidatingWebhookConfigurationobject, depending on the type of webhook you’re implementing. This configuration specifies when the webhook is called and the URL of your webhook server. -
Secure Communication: It’s crucial to secure the communication between the Kubernetes API server and your webhook server. This is typically done using TLS certificates. Kubernetes needs to trust the certificate used by your webhook server, which often involves adding the CA certificate to the API server’s configuration.
Examples
Example 1: Validating Webhook
In this example, we’ll create a simple validating webhook that ensures all pods have a specific label before they are created. We’ll use a Python-based webhook server and the ValidatingWebhookConfiguration object to configure the webhook in Kubernetes.
Step 1: Develop the Webhook Server
First, we’ll create a simple Python-based webhook server using the Flask framework. This server listens for incoming webhook requests and validates the pod creation requests.
from flask import Flask, request, jsonify
app = Flask(__name__)
@app.route('/validate', methods=['POST'])
def validate_pod():
request_info = request.get_json()
pod = request_info['request']['object']
if 'app' not in pod['metadata']['labels']:
return jsonify({'response': {'allowed': False, 'status': {'reason': 'Pod must have an app label'}}})
return jsonify({'response': {'allowed': True}})
Step 2: Configure the Webhook in Kubernetes
Next, we’ll create a ValidatingWebhookConfiguration object to configure the webhook in Kubernetes. This object specifies the URL of the webhook server and the criteria for invoking the webhook.
apiVersion: admissionregistration.k8s.io/v1
kind: ValidatingWebhookConfiguration
metadata:
name: pod-label-validator
webhooks:
- name: pod-label-validator.example.com
clientConfig:
url: https://webhook-server.example.com/validate
caBundle: <base64-encoded-ca-cert>
rules:
- operations: ["CREATE"]
apiGroups: [""]
apiVersions: ["v1"]
resources: ["pods"]
Step 3: Secure Communication
Finally, we need to ensure secure communication between the Kubernetes API server and the webhook server. This involves obtaining a TLS certificate for the webhook server and configuring the API server to trust the certificate.
Example 2: Mutating Webhook
In this example, we’ll create a mutating webhook that automatically adds a specific label to all pods before they are created. We’ll use a Python-based webhook server and the MutatingWebhookConfiguration object to configure the webhook in Kubernetes.
Step 1: Develop the Webhook Server
We’ll create a simple Python-based webhook server using the Flask framework. This server listens for incoming webhook requests and modifies the pod creation requests to add a specific label.
from flask import Flask, request, jsonify
app = Flask(__name__)
@app.route('/mutate', methods=['POST'])
def mutate_pod():
request_info = request.get_json()
pod = request_info['request']['object']
pod['metadata']['labels']['app'] = 'my-app'
return jsonify({'response': {'allowed': True, 'patchType': 'JSONPatch', 'patch': '[{"op": "add", "path": "/metadata/labels/app", "value": "my-app"}]'}})
Step 2: Configure the Webhook in Kubernetes
Next, we’ll create a MutatingWebhookConfiguration object to configure the webhook in Kubernetes. This object specifies the URL of the webhook server and the criteria for invoking the webhook.
apiVersion: admissionregistration.k8s.io/v1
kind: MutatingWebhookConfiguration
metadata:
name: pod-label-mutator
webhooks:
- name: pod-label-mutator.example.com
clientConfig:
url: https://webhook-server.example.com/mutate
caBundle: <base64-encoded-ca-cert>
rules:
- operations: ["CREATE"]
apiGroups: [""]
apiVersions: ["v1"]
resources: ["pods"]
Step 3: Secure Communication
Finally, we need to ensure secure communication between the Kubernetes API server and the webhook server. This involves obtaining a TLS certificate for the webhook server and configuring the API server to trust the certificate.
Example 3: GO Webhook Server
func main() {
// handle our core application
http.HandleFunc("/validate-pods", ServeValidatePods)
http.HandleFunc("/mutate-pods", ServeMutatePods)
http.HandleFunc("/health", ServeHealth)
logrus.Print("Listening on port 443...")
logrus.Fatal(http.ListenAndServeTLS(":443", cert, key, nil))
}
Practical Applications
Webhooks in Kubernetes offer a wide range of practical applications, enabling you to automate and secure your cluster operations. Here are some common use cases for webhooks:
-
Enforcing Policies: Use validating webhooks to enforce policies such as resource naming conventions, security controls, or compliance requirements. For example, you can ensure that all pods have specific labels, or that certain resources are not created in specific namespaces.
-
Customizing Resources: Use mutating webhooks to automatically add annotations, labels, or default values to resources. This can help standardize resource configurations and simplify operational tasks.
-
Integrating with External Systems: Webhooks can be used to integrate Kubernetes with external systems, such as configuration management tools, security scanners, or custom automation workflows. For example, you can use a webhook to automatically update a configuration management database when a new resource is created.
Common Issues
- Webhook Timeouts: Webhooks may fail to respond within the configured timeout period, causing requests to the API server to fail.
- Certificate Problems: Issues with TLS certificates (e.g., expiry, misconfiguration) can prevent the API server from securely communicating with the webhook server.
- Incorrect Configuration: Misconfigurations in the webhook setup can lead to unintended behavior, such as incorrect resource modifications or rejections.
How to Troubleshoot These Issues
- Monitor Logs: Check the logs of your webhook server and the Kubernetes API server. The API server logs can provide insights into why a webhook request failed.
- Review Webhook Configuration: Ensure your webhook configurations (
MutatingWebhookConfigurationandValidatingWebhookConfiguration) are correct and reflect your intentions. - Check Certificates: Verify that your TLS certificates are valid, not expired, and correctly installed/configured on both the webhook server and the Kubernetes API server.
- Use Kubernetes Debugging Tools: Tools like
kubectl describeandkubectl getcan help inspect the state of webhook configurations and identify misconfigurations or errors. - Allow webhook to fail open: If your webhook is causing issues, you can configure it to fail open (i.e., allow all requests) to prevent it from blocking legitimate operations. You can set the
failurePolicyfield toIgnorein your webhook configuration. This should be used as a temporary measure while you investigate and resolve the underlying issues. For example:kubectl edit validatingwebhookconfiguration <webhook-name>and setfailurePolicy: Ignore. - Temporarily Disable Webhooks: If you’re experiencing issues with your webhooks, you can temporarily disable them to allow operations to proceed while you investigate the root cause. Make sure to backup the original configuration before deleting it. For example:
kubectl get validatingwebhookconfiguration <webhook-name> -o yaml > validatingwebhookconfiguration.yamland thenkubectl delete validatingwebhookconfiguration <webhook-name>. - etcd restore blocked by webhook: If a webhook is blocking the restore of etcd, you can temporarily disable the webhook by setting the
failurePolicyfield toIgnorein your webhook configuration. This should be used as a temporary measure while you investigate and resolve the underlying issues. For example:kubectl edit validatingwebhookconfiguration <webhook-name>and setfailurePolicy: Ignore. This is because the webhook is blocking pods from being created, which is required for the etcd restore process including the webhook itself. This gets into a chicken and egg problem. - Use Admission Control Dry Run: You can use the
--dry-run=serverflag withkubectlto simulate the admission control process without actually creating the resource. This can help you understand how your webhooks are affecting resource creation without making any changes to the cluster.
Conclusion
Webhooks offer a versatile and powerful toolset for extending Kubernetes’ capabilities, enabling dynamic, automated responses to cluster events. By understanding and implementing admission and mutating webhooks, developers and operators can significantly enhance the automation, security, and compliance of their Kubernetes clusters. Whether you’re enforcing policies, customizing resources, or integrating with external systems, webhooks provide a critical bridge between Kubernetes and your operational workflows.
Remember, with great power comes great responsibility. Properly securing and testing your webhooks is crucial to maintaining the integrity and reliability of your cluster operations. Happy automating!